SCIM User Provisioning
Learn how to leverage the Starmind Entra Gallery app to setup Starmind automatic user management in minutes
Starmind supports System for Cross-domain Identity Management (SCIM 2.0) provisioning with Azure Entra ID (former Azure Active Directory). The SCIM protocol simplifies the process of creating and managing user accounts in Starmind. When you add, update, or remove users in Entra ID, SCIM automatically propagates these changes to the configured Starmind network.
Requirements
- Your Identity Provider is Azure Active Directory.
- Users in your Active Directory have the following properties:
- Email (the matching attribute)
- First Name
- Last Name
Configuration
Here is Microsoft tutorial: Configure Starmind for automatic user provisioning
To configure SCIM provisioning, you will need an API key, which you can receive from your Solution Architect.
- Sign in to the Azure Portal. In Entra ID, select Enterprise Application, then select All applications.
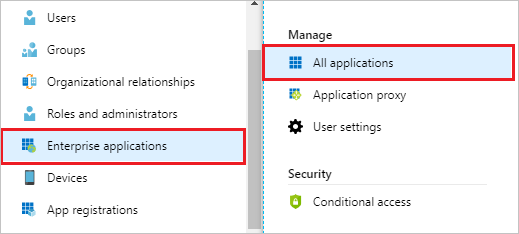
- Select New application.
- Search for Starmind
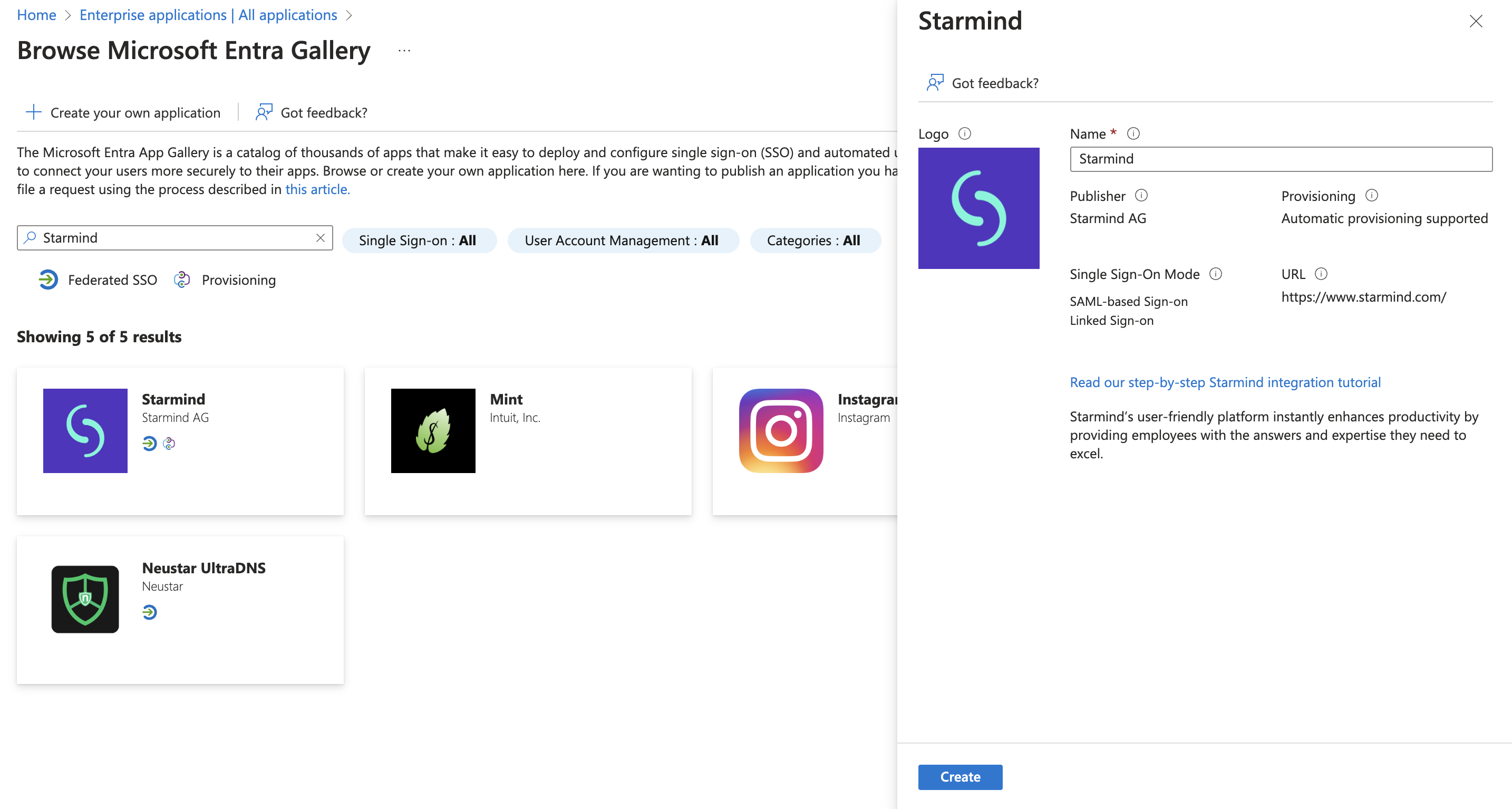
- Click Create.
- Select Provisioning.
- Select Get started.

- Select Provisioning Mode -> Automatic.
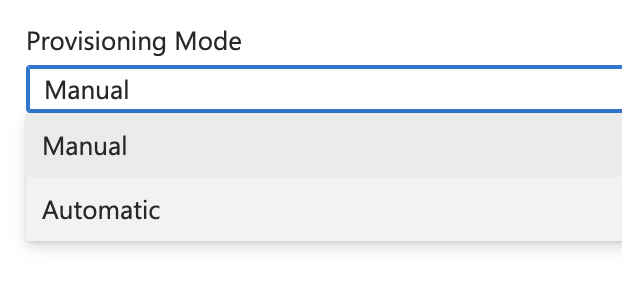
- Under the Admin Credentials section, input the SCIM Base URL for your network in Tenant URL and the API key provided by Starmind in secret token. Click Test Connection to ensure that Entra ID can connect to Starmind. If the connection fails, ensure that your provided credentials are correct or get in touch with your Solution Architect.
Tenant URL: https://<the-network-subdomain>.starmind.com/accounts/api/v1/scim
Secret Token: ApiKeyprovided by Starmind
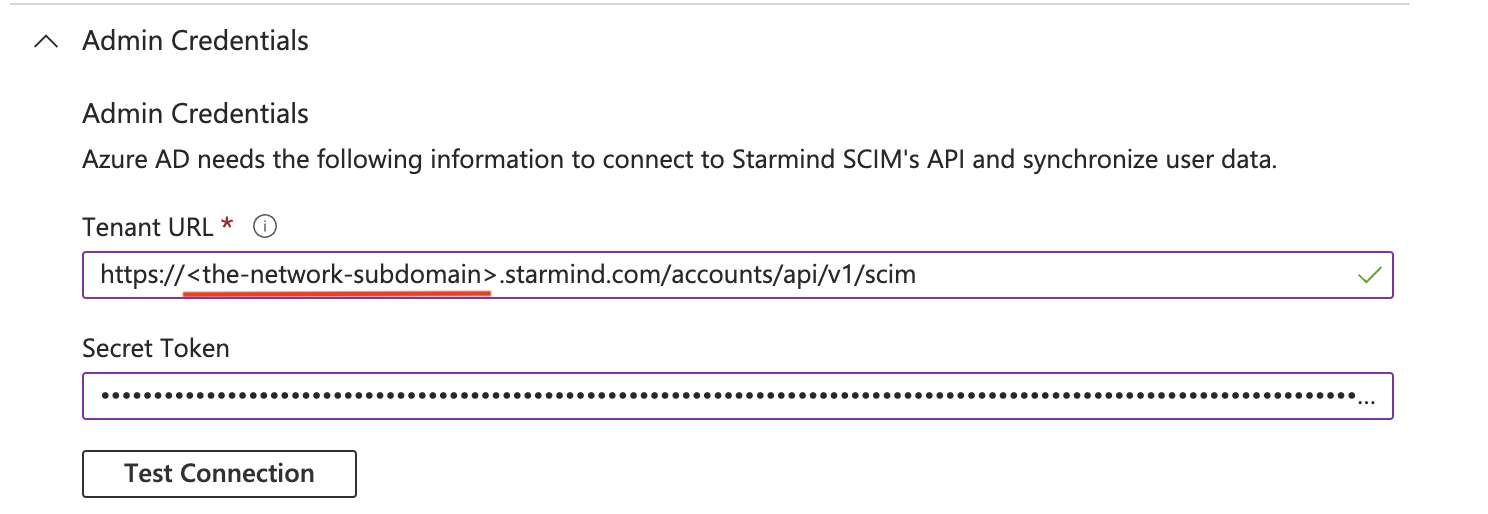
- In the Settings -> Notification Email field, enter the email address of a person or group who should receive the provisioning error notifications and check the Send an email notification when a failure occurs box.
- Click Save.
- Under the Mappings section, select Provision Azure Active Directory Users.

- The attribute mapping can now be configured.
-
Set Enabled to Yes.
-
Disable/enable target object actions (actions on users.) based on your requirements. We commended the following configuration, which will create, update and deactivate users on Starmind but never delete / anonymize them. For information can be found in the user deprovisioning section.
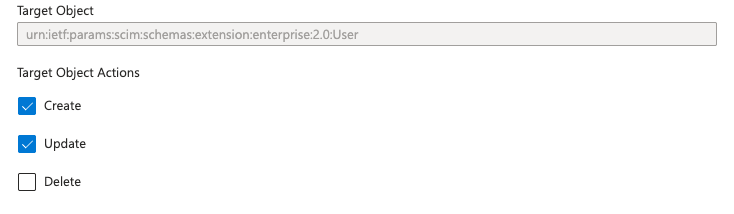
-
In the Attribute Mapping table, search for the userPrincipalName attribute in the left column and click on it. A form will show the details of this attribute. SelectMatch objects using this attribute -> No and click OK.
-
In the Attribute Mapping table, search for the mail attribute in the left column and click on it. Select Match objects using this attribute -> Yes, enter Matching precedence -> 1 and click OK.
-
Configure the remaining Attribute Mapping. This image and table below, demonstrate the correct attribute mapping for Starmind.
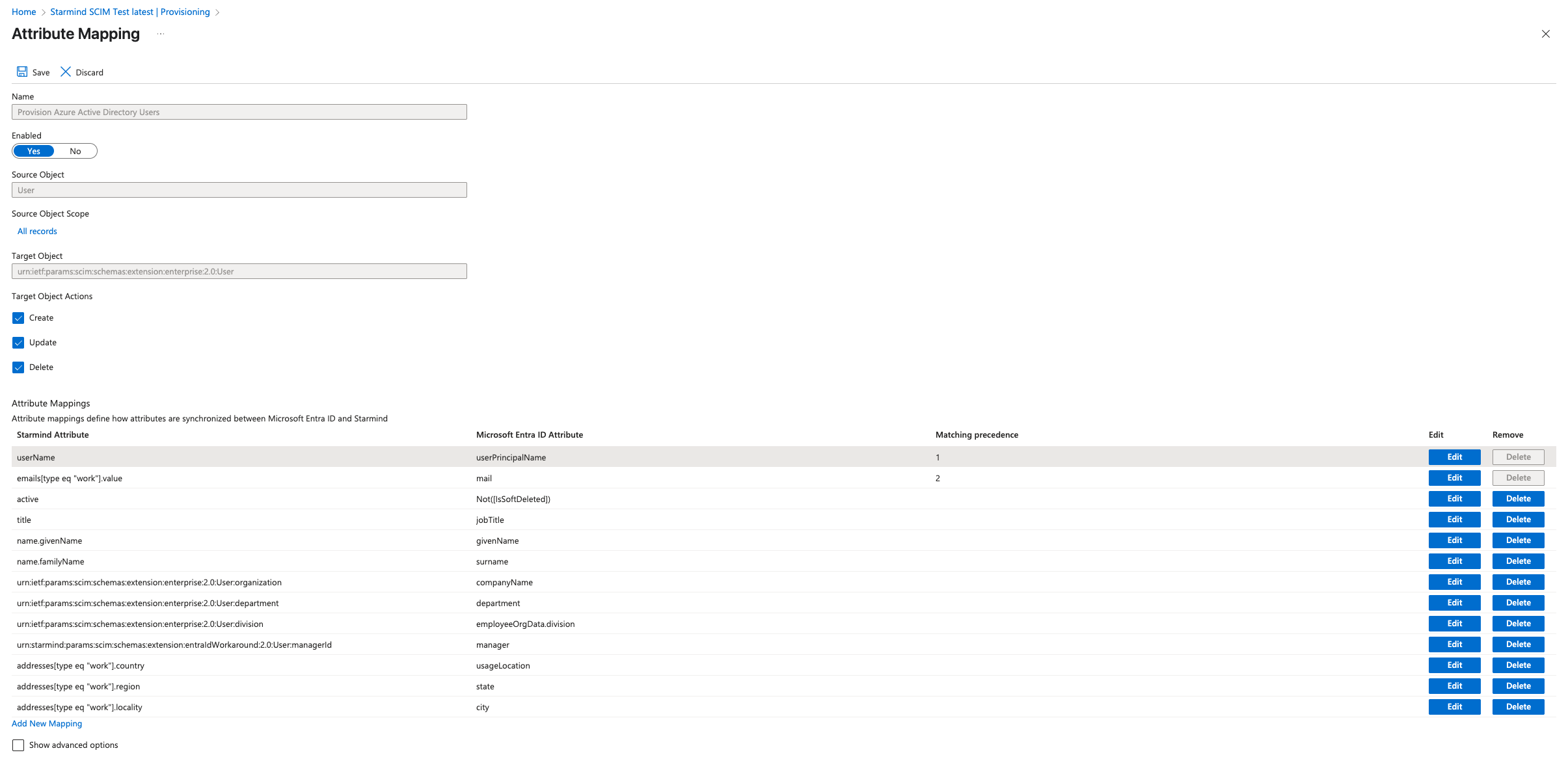
| Starmind Attribute (SCIM) | Microsoft Entra ID Attribute |
|---|---|
| userName | userPrincipalName |
| emails[type eq "work"].value | |
| active | Not([IsSoftDeleted]) |
| title | jobTitle |
| name.givenName | givenName |
| name.familyName | surname |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:organization | companyName |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:division | employeeOrgData.division |
| urn:ietf:params:scim:schemas:extension:enterprise:2.0:User:department | department |
| urn:starmind:params:scim:schemas:extension:entraIdWorkaround:2.0:User:managerId | manager |
| addresses[type eq "work"].country | usageLocation |
| addresses[type eq "work"].region | state |
| addresses[type eq "work"].locality | city |
- Save all changes.
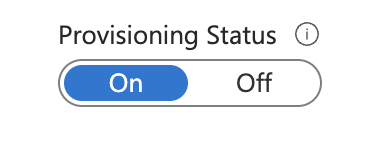
- To enable the Entra ID provisioning service for Starmind, change the Provisioning Status to On in the Settings section.
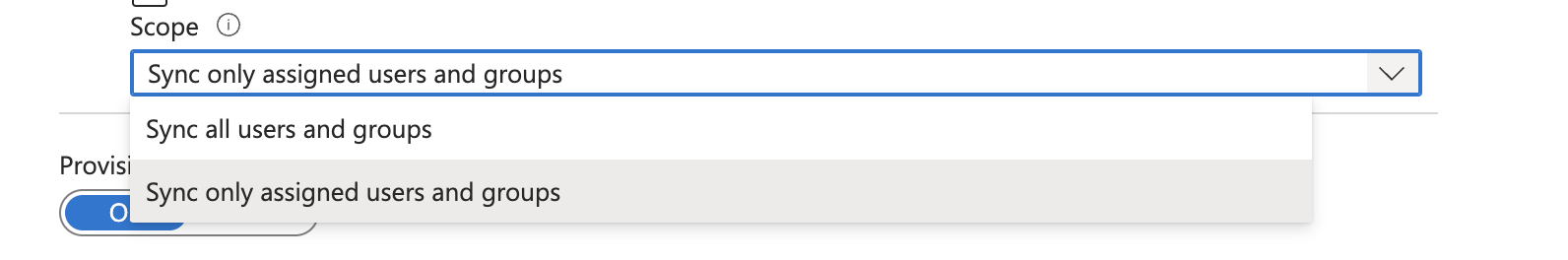
- Define the users that you would like to provision to Starmind by choosing the desired values in Scope in the Settings section.
- When you are ready to provision, click Save.
User initial provisioning
This operation starts the initial synchronization of assigned users defined in Scope in the Settings section. The initial sync takes longer to perform than subsequent syncs, which occur approximately every 40 minutes as long as the Entra ID provisioning service is running. You can use the Synchronization Details section to monitor progress and follow links to the provisioning activity report, which describes all actions performed by the Entra ID provisioning service on Starmind.
User deprovisioning
Users and groups can be deprovisioned by removing them from the Scope in the Settings section. This immediately deactivates the affected users in Starmind. Deactivated users can no longer sign in.
If a user is disabled in Entra ID, the user is automatically deactivated in Starmind, provided the Target Object Action Update is enabled. Note that a user is always disabled in Entra ID when the account is deleted.
If a user is deleted in Entra ID and the Target Object Action Delete is configured, the user is permanently removed from Starmind through anonymization. This action is irreversible.
Further resources
System for Cross-domain Identity Management (SCIM) explained by Microsoft
SCIM 2.0 standard
Addendum
Notes on Attribute mappings
addresses[type eq "work"].countryhas to be mapped tousageLocationand notcountrybecause according to the SCIM spec, it needs to be aISO 3166-1 alpha-2country code. By default, Entra ID'scountryattribute is the full country name.urn:starmind:params:scim:schemas:extension:entraIdWorkaround:2.0:User:managerIdis a custom Starmind schema attribute used as a workaround forurn:ietf:params:scim:schemas:extension:enterprise:2.0:User:manager.value. This is necessary because Microsoft Entra ID does not support writing to complex or multiValued SCIM attributes such asmanager. See: Microsoft Q&A.
Updated about 1 month ago