Microsoft Teams
The Microsoft Teams connector uses messages in public channels to build accurate expertise profiles.
Why connectors? Data sources and connectors are critical to Starmind's Knowledge Engine and our ability to build accurate expertise profiles for all your employees. With every data source connected to Starmind's Knowledge Engine, the accuracy of expertise profiles and our Expert Search improves dramatically.
With our Microsoft Teams connector, Starmind can analyse conversations to enhance each individual's expertise profile. The connector learns exclusively from public teams and shared channels, ensuring users' privacy by not invading private conversations.
Learn more about public and private teams in Microsoft Teams
Learn more about teams and channels in Microsoft Teams
Data Retention and Privacy
By default, Starmind does not store the textual content of MS Teams channels. Only the users (email), extracted topics, and metadata (e.g., URL) are retained.
However, we recommend activating encrypted content storage if you want to enhance the quality of topic detection and personalization. Storing full document text (in encrypted form) allows our AI systems to build richer context for customer-specific terminology. This leads to significantly improved topic mapping and Knowledge Graph performance.
Access Control via Technical User Account
Starmind requires a dedicated technical user account to retrieve data from your MS Teams instance. Our connector uses Microsoft Graph delegated permissions, meaning it can only access teams and channels, which the technical user can access. Additionally, the connector disregards private teams, private channels, and one-on-one conversations.
This ensures you remain in control — you can revoke access immediately by adjusting the technical user’s permissions or removing the account.
Required Permissions and Consent
To function correctly, the connector requires read access to Microsoft Teams. During the setup, you will log in with your Microsoft Tenant using the technical user account and explicitly grant consent to the required permissions.
Below is the list of required delegated Microsoft Graph permissions and what they allow:
Group.Read.All: Allows the app to list groups and to read their properties and all group memberships on behalf of the technical user. It also allows the app to read calendars, conversations, files, and other group content for all groups the technical user can access.Directory.Read.All: Allows the app to read data in your organization's directory, such as users, groups, and apps. Note: Users may consent to applications that require this permission if the application is registered in their own organization’s tenant.User.Read.All: Allows the app to read data in your organization's directory, such as users, groups, and apps. Note: Users may consent to applications that require this permission if the application is registered in their own organization’s tenant.ChannelMessage.Read.All: Allows the app to read the full set of profile properties, reports, and managers of other users in your organization, on behalf of the signed-in user.offline_access: Maintain access to data you have given it access to. Allows the app to see and update the data you gave it access to, even when you are not currently using it. This does not give the app any additional permissions.
More information about Microsoft Graph permissions can be found here: https://learn.microsoft.com/en-us/graph/permissions-reference?view=graph-rest-beta
In addition to the privileges, the API restricts access to groups where the configured technical user is a member (enforced by the MS Graph API). This gives the customer more control over limiting access to the groups relevant to the connector.
Integrating with Microsoft Teams
1. Setting Up the Technical User for Starmind’s Teams Connector
To ensure a secure and controlled connection between Starmind and Microsoft Teams, we recommend creating a dedicated technical user account in your Microsoft 365 environment. This account is used exclusively for the Starmind connector and should follow best practices for service accounts.
Recommended Approach:
- Create a Dedicated User Account
- Set up a new Microsoft Entra ID (formerly Azure AD) account, such as [email protected].
- Assign the Necessary Permissions
- Add this technical user to only the Teams and Channels that should be accessible by Starmind. This minimizes exposure and ensures compliance with internal data policies.
- Grant the required permissions (as outlined above) through Microsoft Entra ID or during the consent process.
- Apply Security Best Practices
- Enable Multi-Factor Authentication (MFA) if your organization requires it for all accounts.
- Use Conditional Access Policies to restrict when and where this account can be used.
- Consider disabling email and interactive login to limit its usage to API-based access only.
- Document & Monitor Usage
- Maintain internal documentation about the account’s purpose and permissions.
- Set up monitoring and alerts in Microsoft Entra ID to track unexpected activity.
- Assign responsibility for reviewing access periodically to ensure compliance.
By following this approach, you keep control over the connector’s access while maintaining security and flexibility.
2. Connecting Starmind to Teams
- From the left-hand navigation panel, select Admin and then Integrations
- From the Available tab, search for MS Teams
- Select Connect
- Use the credentials of a dedicated technical user to log into your Microsoft 365 environment.
- Accept the terms of the integration and grant the requested permissions.
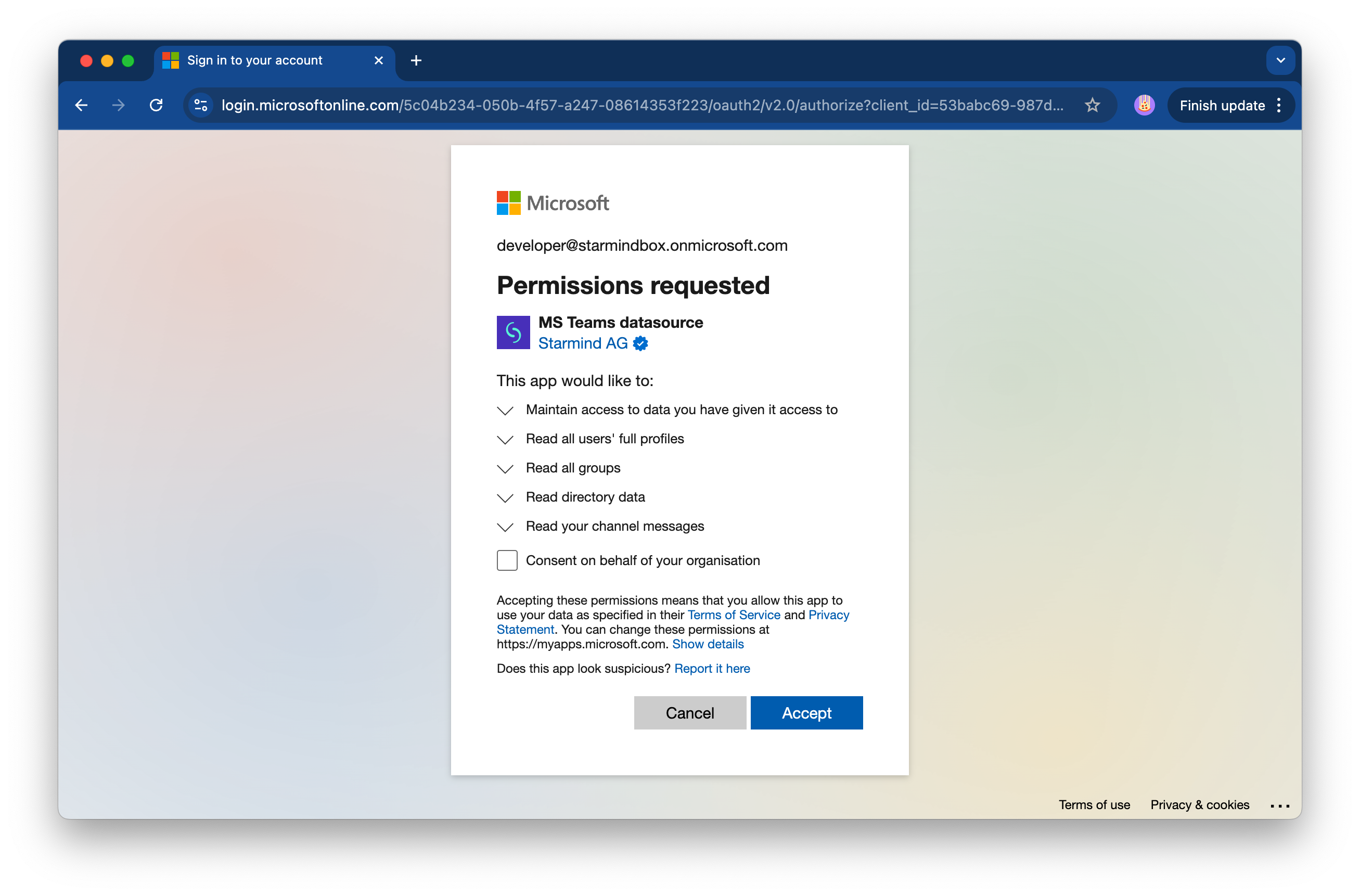
- Once connected, the system automatically starts processing the data it has access to and starts building an accurate expertise profile for each individual
Updated 2 days ago
